Pass The Hash Attack
10 cobalt strike can perform pass the hash. Pass the hash attack is an attack in which the attacker hacks a users password and breaks into the server or service to steal data or do other malicious activities.
Dissecting The Pass The Hash Attack
11 apt32 has used pass the hash for lateral movement.

Pass the hash attack. What are pass the hash attacks. 7 hoplight has been observed loading several apis associated with pass the hash. This means that even after performing ntlm authentication successfully using the pass the hash technique tools like sambas smb client might not have implemented the functionality the attacker might want to use. 4 empire can perform pass the hash attacks. The password is converted into a hash value using some popular hash algorithm and then the computed hash value. The apt1 group is known to have used pass the hash. A pass the hash attack is an expoit in which an attacker steals a hashed user credential and without cracking it reuses it to trick an authentication system into creating a. Introduction as a security practitioner it is common to focus a great deal of your time on ensuring that password. The attack creates or simulates an it problem on an infected endpoint. How the pass the hash attack technique works and a demonstration of the process that can be used to take stolen password hashes and use them successfully without having to crack their hidden contents. This document discusses pass the hash pth attacks against the windows operating systems and provides holistic planning strategies that when combined with the windows security features will provide a more effective defense against pass the hash attacks. With the wide access granted an attacker can disrupt information systems by implanting malware on target machines steal confidential and critical data and cease operations on critical servers. This endpoint belongs to a privileged access user. This meant that it was difficult to attack windows programs that use dcom or rpc. First we need to define pass the hash attacks.
 What Is Pass The Hash Attack The Security Buddy
What Is Pass The Hash Attack The Security Buddy
 Can An Intruder Still Possibly Succeed With Pass The Hash Or Pass
Can An Intruder Still Possibly Succeed With Pass The Hash Or Pass
 What Is Pass The Hash Attack And How To Mitigate It Ammar Hasayen
What Is Pass The Hash Attack And How To Mitigate It Ammar Hasayen
 What Is A Pass The Hash Attack Youtube
What Is A Pass The Hash Attack Youtube
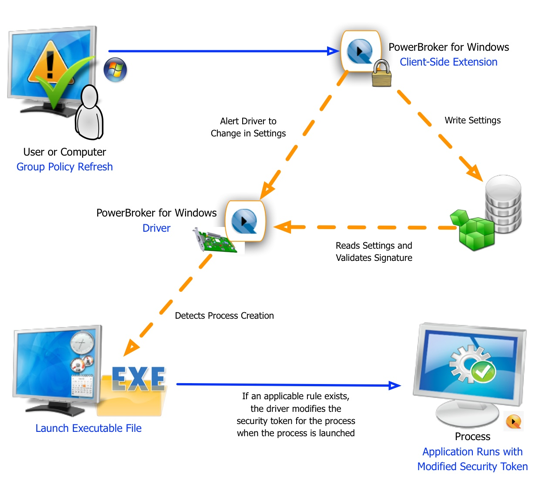 How To Stop Pass The Hash Attacks On Windows Desktops Beyondtrust
How To Stop Pass The Hash Attacks On Windows Desktops Beyondtrust
 What Is Pass The Hash Attack And How To Mitigate It Ammar Hasayen
What Is Pass The Hash Attack And How To Mitigate It Ammar Hasayen
Https Www Sans Org Reading Room Whitepapers Testing Pass The Hash Attacks Tools Mitigation 33283
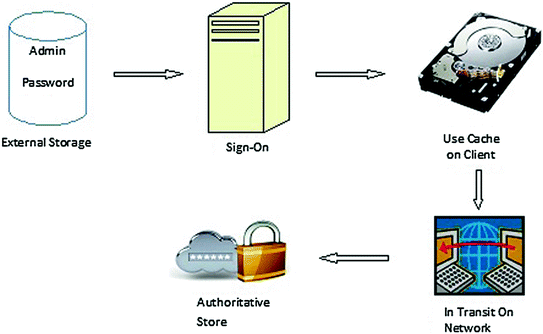 Analysis And Impact Of Different Mechanisms Of Defending Pass The
Analysis And Impact Of Different Mechanisms Of Defending Pass The
 What Is Pass The Hash Attack And How To Mitigate It Ammar Hasayen
What Is Pass The Hash Attack And How To Mitigate It Ammar Hasayen
 Security Thoughts Pass The Hash And Other Credential Theft The
Security Thoughts Pass The Hash And Other Credential Theft The
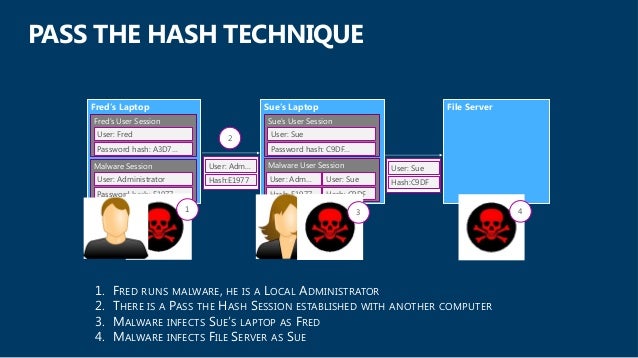 How Cyber Criminals Steal Passwords Via Pass The Hash And Other Attac
How Cyber Criminals Steal Passwords Via Pass The Hash And Other Attac
 New Strategies And Features To Help Organizations Better Protect
New Strategies And Features To Help Organizations Better Protect
 What Is Pass The Hash Attack And How To Mitigate It Ammar Hasayen
What Is Pass The Hash Attack And How To Mitigate It Ammar Hasayen
 Forensic Artifacts From A Pass The Hash Pth Attack Ppt Download
Forensic Artifacts From A Pass The Hash Pth Attack Ppt Download
 Global Survey Reveals True Impact Of Pass The Hash Attacks One
Global Survey Reveals True Impact Of Pass The Hash Attacks One
 Combining Responder And Psexec For Internal Penetration Tests
Combining Responder And Psexec For Internal Penetration Tests
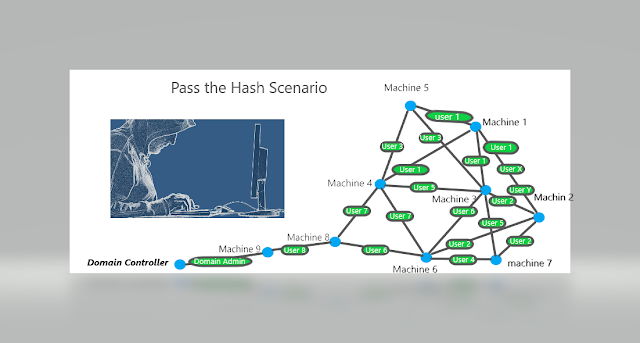 Pass The Hash Attack Varun Upadhyay Medium
Pass The Hash Attack Varun Upadhyay Medium
 Hacks Weekly 4 Pass The Hash Attack Tutorial Youtube
Hacks Weekly 4 Pass The Hash Attack Tutorial Youtube
 Forensic Artifacts From A Pass The Hash Pth Attack By Gerard
Forensic Artifacts From A Pass The Hash Pth Attack By Gerard
Https Www Sans Org Reading Room Whitepapers Testing Pass The Hash Attacks Tools Mitigation 33283
 Performing Pass The Hash Attacks With Mimikatz Insider Threat Blog
Performing Pass The Hash Attacks With Mimikatz Insider Threat Blog
 What Is Pass The Hash Attack The Security Buddy
What Is Pass The Hash Attack The Security Buddy
Https Media Blackhat Com Bh Us 12 Briefings Duckwall Bh Us 12 Duckwall Campbell Still Passing Wp Pdf
 Performing Pass The Hash Attacks With Mimikatz Insider Threat Blog
Performing Pass The Hash Attacks With Mimikatz Insider Threat Blog
 What Is Pass The Hash Attack And How To Mitigate It Ammar Hasayen
What Is Pass The Hash Attack And How To Mitigate It Ammar Hasayen
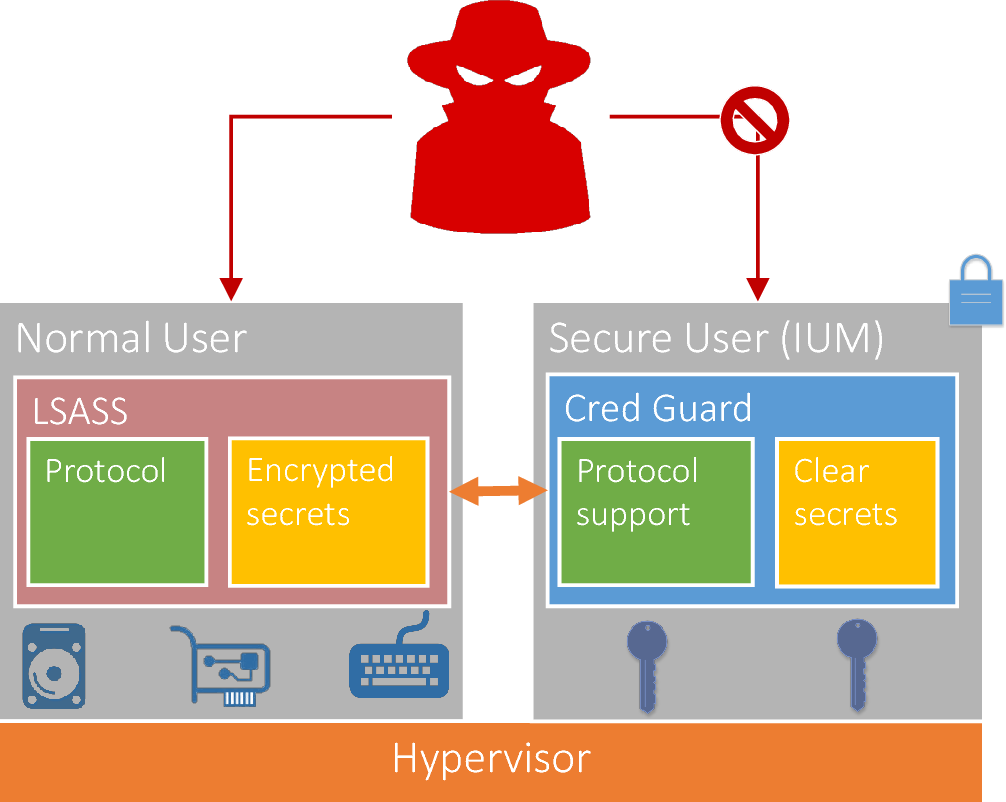 Pass The Hash Semantic Scholar
Pass The Hash Semantic Scholar
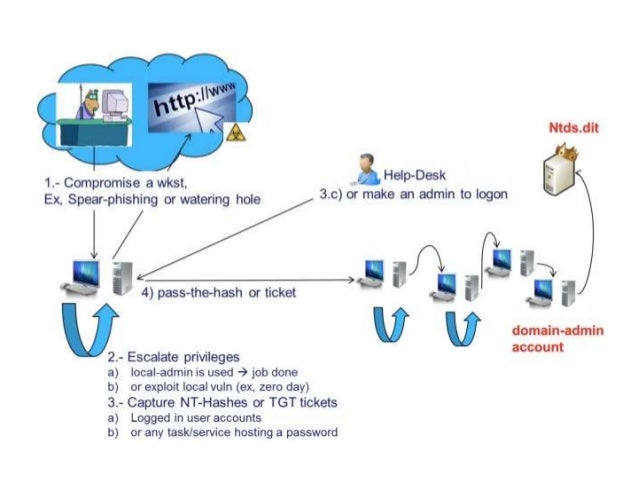 Golden Ticket Pass The Ticket Mi Tm Kerberos Attacks Explained
Golden Ticket Pass The Ticket Mi Tm Kerberos Attacks Explained
 How To Perform A Pass The Hash Attack Get System Access On
How To Perform A Pass The Hash Attack Get System Access On
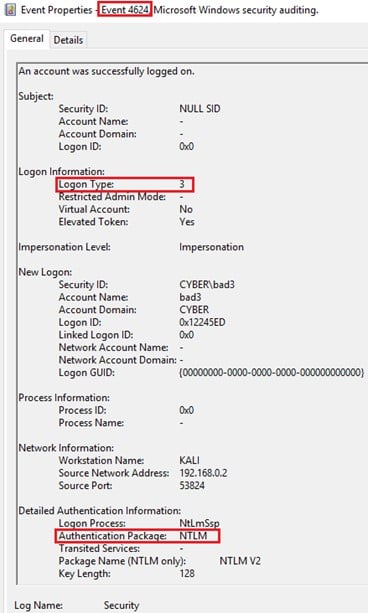 Detecting Pass The Hash With Windows Event Viewer Cyberark
Detecting Pass The Hash With Windows Event Viewer Cyberark
 Pass The Hash Attack Getting Windows Server Credentials Youtube
Pass The Hash Attack Getting Windows Server Credentials Youtube
 Pdf Implementation And Mitigation Of Various Tools For Pass The
Pdf Implementation And Mitigation Of Various Tools For Pass The
 Pass The Hash Attack Penetration Testing Lab
Pass The Hash Attack Penetration Testing Lab
 Pass The Hash Attack Prevalence Shows Urgent Need For Better
Pass The Hash Attack Prevalence Shows Urgent Need For Better
 Using Deception Against Pass The Hash Attacks Avertium Mdr Edr
Using Deception Against Pass The Hash Attacks Avertium Mdr Edr
 Reliably Detecting Pass The Hash Through Event Log Analysis
Reliably Detecting Pass The Hash Through Event Log Analysis
Armitage Tutorial Cyber Attack Management For Metasploit
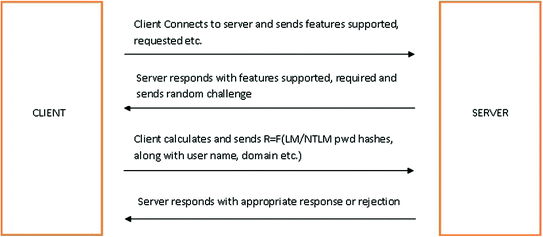 Analysis And Impact Of Different Mechanisms Of Defending Pass The
Analysis And Impact Of Different Mechanisms Of Defending Pass The
 What Is Pass The Hash Attack And How To Mitigate It Ammar Hasayen
What Is Pass The Hash Attack And How To Mitigate It Ammar Hasayen
 Lab Of A Penetration Tester Week Of Evading Microsoft Ata Day 2
Lab Of A Penetration Tester Week Of Evading Microsoft Ata Day 2
Pass The Hash Is Dead Long Live Pass The Hash Harmj0y
In Depth Look Apt Attack Tools Of The Trade Trendlabs Security
 Penetration Testing Explained Part Vi Passing The Hash
Penetration Testing Explained Part Vi Passing The Hash
 Performing Pass The Hash Attacks With Mimikatz Insider Threat Blog
Performing Pass The Hash Attacks With Mimikatz Insider Threat Blog
 Pass The Hash Attack Duro A Morire Antreem
Pass The Hash Attack Duro A Morire Antreem
 Pass The Hash Is Still A Threat Get Stuff Secured
Pass The Hash Is Still A Threat Get Stuff Secured
 Forensic Artifacts From A Pass The Hash Pth Attack
Forensic Artifacts From A Pass The Hash Pth Attack
 Attack Tutorial Pass The Hash Attack Using Mimikatz Youtube
Attack Tutorial Pass The Hash Attack Using Mimikatz Youtube
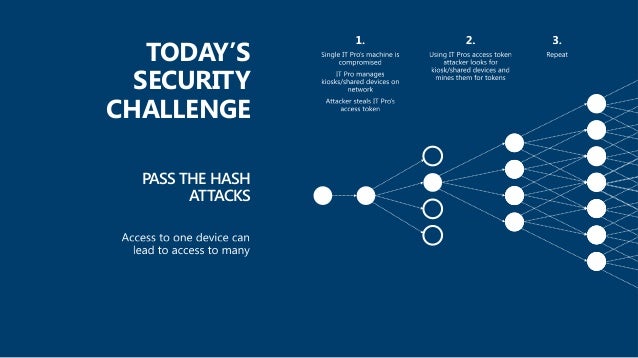 How Cyber Criminals Steal Passwords Via Pass The Hash And Other Attac
How Cyber Criminals Steal Passwords Via Pass The Hash And Other Attac
Https Cert Europa Eu Static Whitepapers Cert Eu Swp 17 002 Lateral Movements Pdf
 Ketshash Is A Little Tool For Detecting Suspicious Privileged Ntlm
Ketshash Is A Little Tool For Detecting Suspicious Privileged Ntlm
 One Identity Global Survey Reveals Pass The Hash Attack
One Identity Global Survey Reveals Pass The Hash Attack
 Pass The Hash Attack Prevalence Shows Urgent Need For Better
Pass The Hash Attack Prevalence Shows Urgent Need For Better
 Pass The Hash Attacks Pass The Hash Mitigation And Network
Pass The Hash Attacks Pass The Hash Mitigation And Network
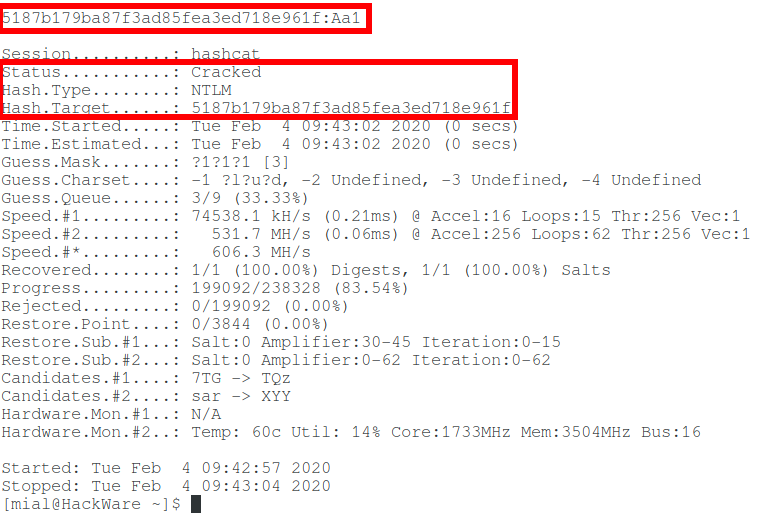 How To Hack A Windows Password Ethical Hacking And Penetration
How To Hack A Windows Password Ethical Hacking And Penetration
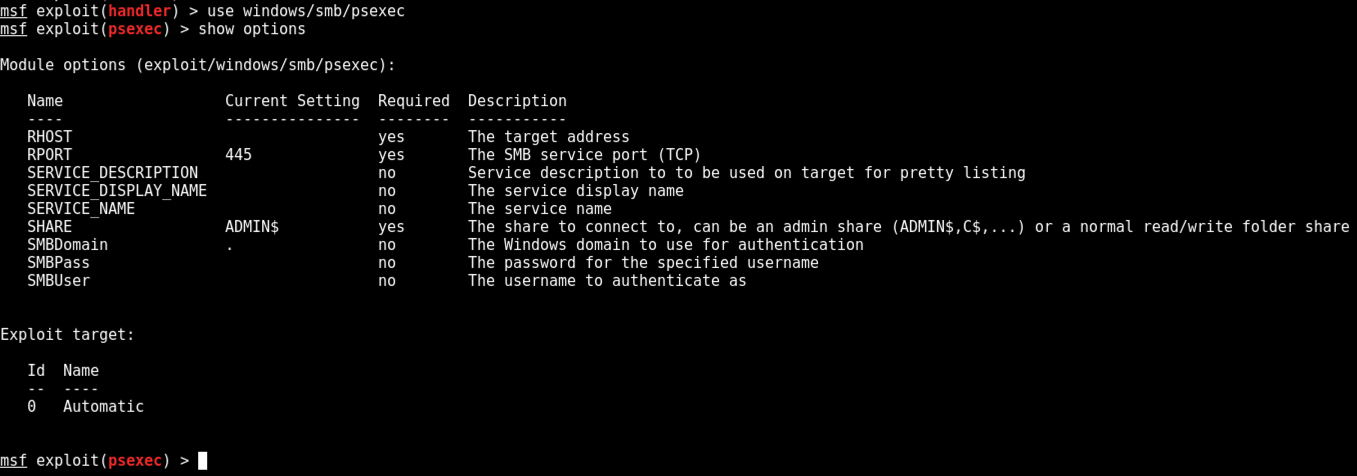 Proj 14x Pass The Hash 10 Pts Extra Credit
Proj 14x Pass The Hash 10 Pts Extra Credit
 Kerberos Attack How To Stop Golden Tickets
Kerberos Attack How To Stop Golden Tickets
 Pass The Hash Attack Duro A Morire Antreem
Pass The Hash Attack Duro A Morire Antreem
Https Www Sans Org Reading Room Whitepapers Testing Crack Pass Hash 33219
 Pass The Hash Attack Archives Security Affairssecurity Affairs
Pass The Hash Attack Archives Security Affairssecurity Affairs
 Performing Pass The Hash Attacks With Mimikatz Insider Threat Blog
Performing Pass The Hash Attacks With Mimikatz Insider Threat Blog
 Preet Shah Pass The Hash Pth Attack Corporate Attack
Preet Shah Pass The Hash Pth Attack Corporate Attack
 Azure Atp Security Alert Lateral Movement Playbook Microsoft Docs
Azure Atp Security Alert Lateral Movement Playbook Microsoft Docs
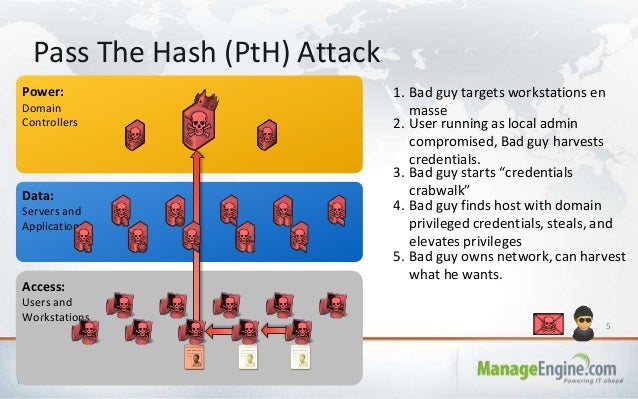 Protecting Windows Passwords And Preventing Windows Computer Passwo
Protecting Windows Passwords And Preventing Windows Computer Passwo
 Windows Event Ids For Incident Response Cases Alparslan Akyildiz
Windows Event Ids For Incident Response Cases Alparslan Akyildiz
 Pass The Hash Detection Native Windows Event Logs Pass The
Pass The Hash Detection Native Windows Event Logs Pass The
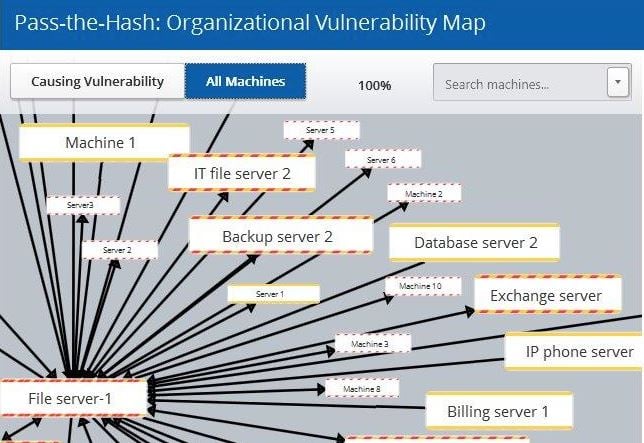 What S Your Privileged Account Attack Surface Cyberark
What S Your Privileged Account Attack Surface Cyberark
 Top Attacks 3 Local Administrator Attacks Aka Pass The Hash
Top Attacks 3 Local Administrator Attacks Aka Pass The Hash
 How Cyber Criminals Steal Passwords Via Pass The Hash And Other Attac
How Cyber Criminals Steal Passwords Via Pass The Hash And Other Attac
 Pass The Hash Attack Mitigation The Complete Guide Hysolate
Pass The Hash Attack Mitigation The Complete Guide Hysolate
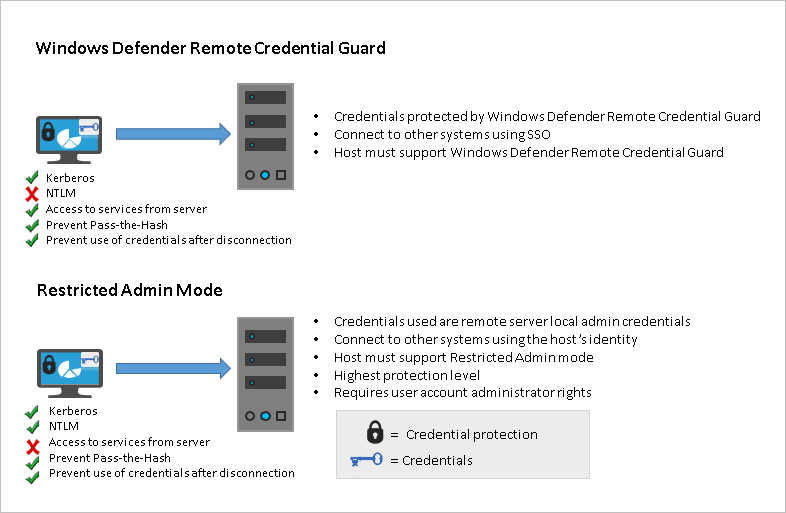 Protect Remote Desktop Credentials With Windows Defender Remote
Protect Remote Desktop Credentials With Windows Defender Remote
 Pass The Hash Detection Native Windows Event Logs Pass The
Pass The Hash Detection Native Windows Event Logs Pass The
 What Is Pass The Hash Attack And How To Mitigate It Ammar Hasayen
What Is Pass The Hash Attack And How To Mitigate It Ammar Hasayen
 Pass The Hash Is Still A Threat Get Stuff Secured
Pass The Hash Is Still A Threat Get Stuff Secured
 Pass The Hash Attack Against Windows Xp Youtube
Pass The Hash Attack Against Windows Xp Youtube
 One Identity Global Survey Reveals Pass The Hash Attack
One Identity Global Survey Reveals Pass The Hash Attack
 Remote Safe Mode Attack Defeats Windows 10 Pass The Hash Defenses
Remote Safe Mode Attack Defeats Windows 10 Pass The Hash Defenses
 One Identity Report Highlights It Security Guru
One Identity Report Highlights It Security Guru
 Codegreen Blog Demonstration Of Pass The Hash Attack
Codegreen Blog Demonstration Of Pass The Hash Attack
 Cynergy Solutions Sdn Bhd What Is Pass The Hash Attack
Cynergy Solutions Sdn Bhd What Is Pass The Hash Attack
 How To Perform A Pass The Hash Attack Get System Access On Windows
How To Perform A Pass The Hash Attack Get System Access On Windows
Pass To Hash Not Working Issue 215 Gentilkiwi Mimikatz Github
 Pass The Hash With Machine Accounts Red Teaming Experiments
Pass The Hash With Machine Accounts Red Teaming Experiments
Pass The Hash Attack Practical Windows Penetration Testing Video
 Azure Atp Security Alert Lateral Movement Playbook Microsoft Docs
Azure Atp Security Alert Lateral Movement Playbook Microsoft Docs
 A Second Preimage Attack On Zipper Hash Chen 2015 Security
A Second Preimage Attack On Zipper Hash Chen 2015 Security
Closer Look Of Cve 2019 1491 Microsoft Sharepoint Server
 Ppt Pass The Hash Gaining Root Access To Your Network
Ppt Pass The Hash Gaining Root Access To Your Network
Pass The Hash Is Dead Long Live Pass The Hash Harmj0y
 Reliably Detecting Pass The Hash Through Event Log Analysis
Reliably Detecting Pass The Hash Through Event Log Analysis
 Ketshash A Little Tool For Detecting Suspicious Privileged Ntlm
Ketshash A Little Tool For Detecting Suspicious Privileged Ntlm
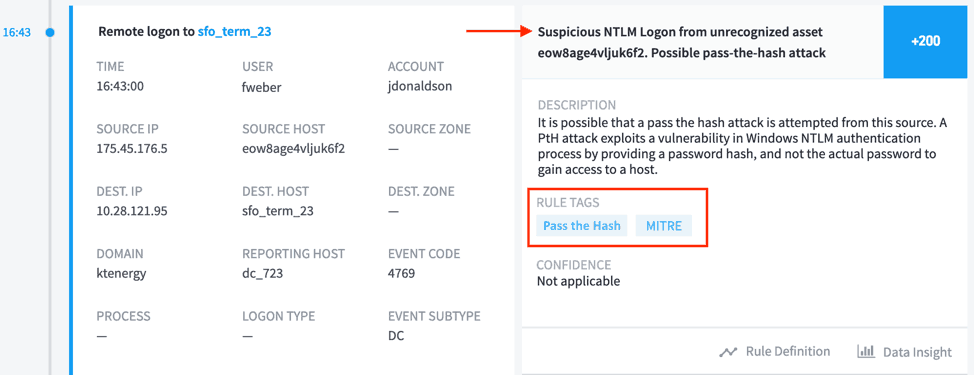 Stop Destroying The Evidence Understanding The Entire Attack Chain
Stop Destroying The Evidence Understanding The Entire Attack Chain
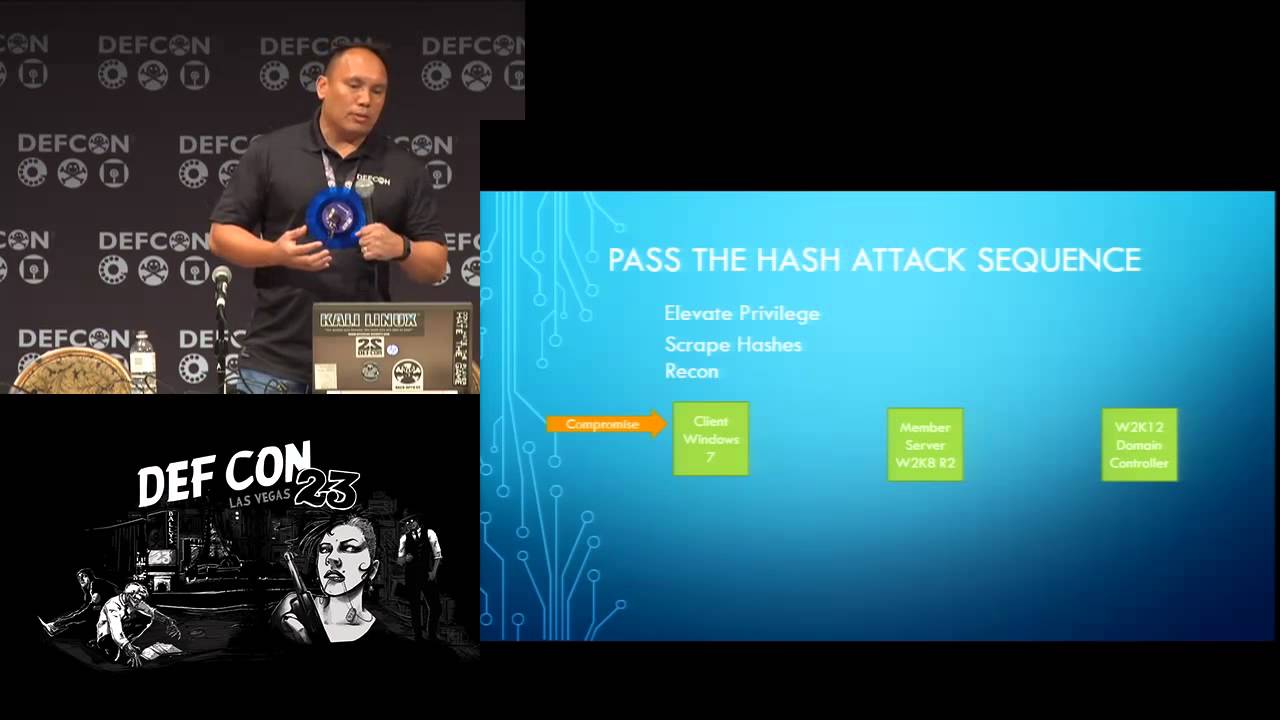 Def Con 23 Gerard Laygui Forensic Artifacts From A Pass The
Def Con 23 Gerard Laygui Forensic Artifacts From A Pass The
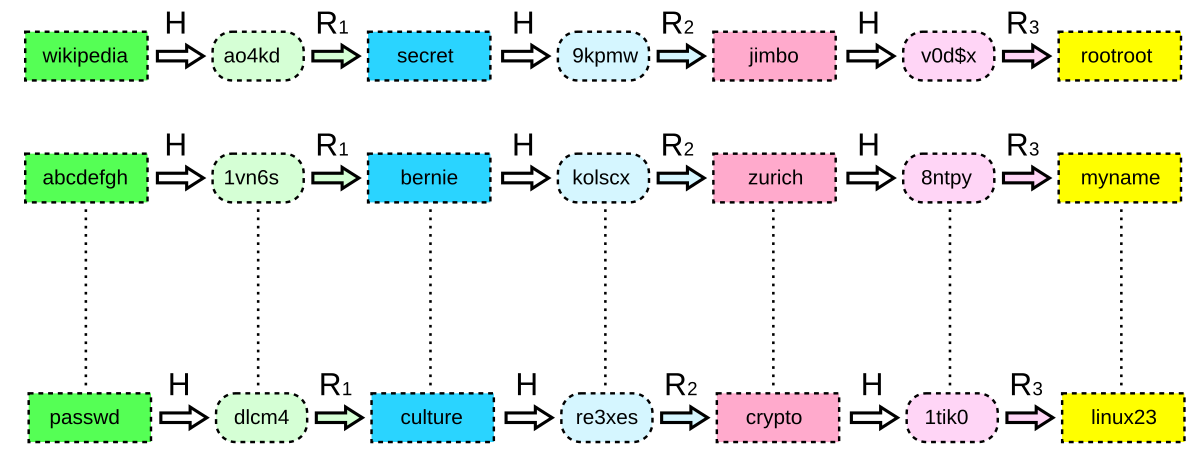
 Understanding Rainbow Table Attack Geeksforgeeks
Understanding Rainbow Table Attack Geeksforgeeks


Tidak ada komentar untuk "Pass The Hash Attack"
Posting Komentar